
Introduction to Network Security: The Digital Stronghold
Picture your network as a sprawling digital kingdom, complete with towering walls, deep moats, and vigilant sentries. This realm, however, is not made of stone and mortar but of data and connectivity. Network security is the array of defensive measures, strategies, and tools deployed to protect this kingdom. It’s crucial because, in the digital era, threats like cyber-attacks are not just possible – they are constantly battering at the gates.
Why Network Security is Imperative?
- Data Protection: Like a treasure vault, our data is precious and sought after by digital marauders.
- Operational Stability: Without security, it’s akin to a castle under relentless siege, vulnerable to chaos and destruction.
- Financial Security: A breach can drain a company’s financial reserves as if raiders had plundered its coffers.
- Intellectual Property Protection: The unique ideas and innovations of a company are its crown jewels, needing vigilant safeguarding.
- Regulatory Compliance: Failing to comply with laws like HIPAA or GDPR can lead to dire consequences, much like defying the king’s edicts.
What is Network layers and security?
Each layer has a specific function and interacts with the layers above and below it. The layers work together to transmit and receive information, allowing communication between devices connected to the network.The OSI model is an interconnection system that is open in nature.As information moves between devices, it travels through these layers, with each layer being vulnerable to various types of cyber threats. Consequently, to ensure overall network security, it is imperative to protect every layer within the stack.
This chart aligns the OSI layers with their respective network security types.
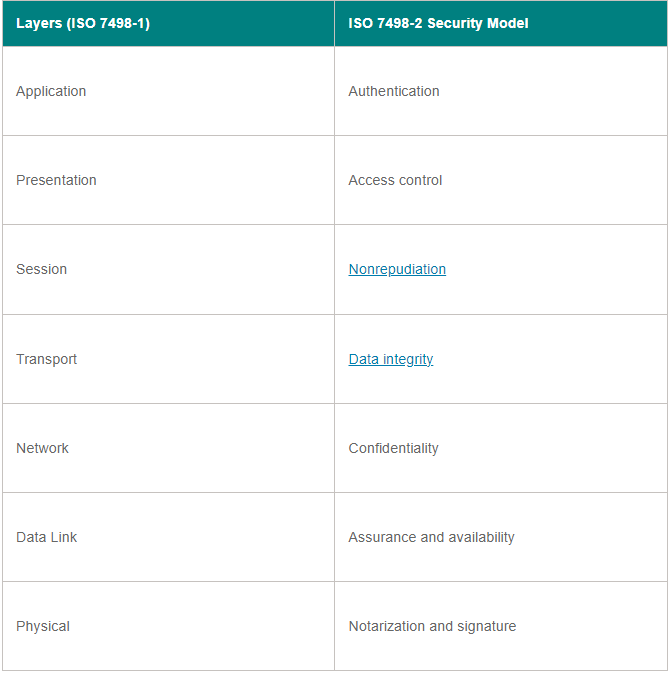
“Network” is used to refer to a specific layer in the computer network, but network security is not limited to just this layer. All devices in a computer network operate on multiple layers while handling data. Therefore, each layer must be protected in order for the network to be deemed secure. In simpler terms, network security extends beyond the Network layer. network The definition of network security in this context does not solely pertain to the network layer, but encompasses the entire corporate infrastructure.
For example, some people may make the Differentiation between the security of cloud computing and the security of network systems.Cloud security encompasses two aspects: application security and container security, both of which operate in a different layer than the network layer in the OSI model. Nevertheless, these cloud functions are still regarded as components of the overall corporate network and their protection falls within the realm of network security.
Major Threats to the Digital Realm
- Malware and Viruses: These are akin to plagues that can debilitate the kingdom’s defenses.
- Phishing Attacks: Deceptive maneuvers designed to infiltrate and pilfer from within.
- Unsecured Wi-Fi: As risky as leaving the castle gates unlocked and unguarded.
- Device Theft: The loss of a device is like losing a piece of the kingdom to adversaries.
- Data Leakage: Vital information slipping out, much like secrets whispered beyond castle walls.
The Arsenal for Defense
Different software and tools used to secure networks.
Deploying a combination of security policies and tools, which may differ depending on the specific network and may evolve over time. Effective security measures frequently require the utilization of diverse strategies. layered security or defense in depth To provide organizations with a wide range of security measures, various types of network security tools and software are frequently utilized.
• Access control. This approach restricts entry to network applications and systems only for a particular set of users and devices, while preventing unauthorized users and devices from gaining access.
• Antivirus and antimalware. Antivirus and antimalware Antivirus programs are specifically built to identify, delete, or stop viruses and malicious software including Trojan horses, ransomware, and spyware, in order to shield a computer and its network from being infected.
• Application security. It is essential to supervise and safeguard the applications utilized by organizations to operate their businesses. Regardless of whether an organization develops or purchases an application, it is important to note that contemporary malware risks frequently take aim at these applications. open source The code and containers are utilized by organizations to create software and applications.
• Behavioral analytics. This technique examines the behavior of networks and identifies any unusual activities, notifying organizations of them automatically.
• Cloud security. Cloud providers often sell add-on cloud security cloud providers offer features and resources to ensure the security of their cloud services. These providers are responsible for managing the security of the entire infrastructure and also provide tools that allow users to safeguard their specific instances within the broader cloud infrastructure. Amazon Web Services offers security groups that manage the flow of incoming and outgoing traffic linked to an application or resource.
• Data loss prevention (DLP). These tools are designed to observe and stop any unauthorized access or disclosure of data, regardless of whether it is actively being used, transferred, or stored. DLP The most critical and vulnerable data is frequently categorized and employees are trained in effective methods to safeguard it. For example, a recommended practice includes refraining from sending important files as email attachments.
• Email security. cyberattacks through email phishing scams and malware attachments. These attacks can lead to information breaches, financial loss, and system compromises. Email security measures must be implemented to protect sensitive data and prevent unauthorized access. phishing Employees unknowingly expose themselves to malware attacks by clicking on email links that discreetly install harmful software. Additionally, they unintentionally use email as an insecure means of transmitting files and sensitive information.
• Firewall. Software or firmware examines incoming and outgoing data to stop unauthorized access to a network. Firewalls are commonly used security tools that are placed in various locations throughout the network.Next-generation firewalls provide enhanced security measures.protecting against attacks at the application layer and defending against advanced malware using inline deep packet inspection.
• Intrusion detection system (IDS) is a security mechanism designed to identify unauthorized access or malicious activities within a computer network. An IDS An IDS identifies and signals potentially harmful unauthorized entry attempts, while not eliminating them. Typically, both an IDS and an intrusion prevention system (IPS) are employed alongside a firewall.
• Intrusion prevention system. IPSes The purpose of these systems is to stop unauthorized individuals from accessing a network by identifying and stopping any attempts made to breach it.
• Mobile device security. ensuring network security. The advent of business applications specifically designed for smartphones and other mobile devices has elevated the significance of these devices in maintaining network security. It is essential to carefully track and regulate the devices that are granted access to a network and closely monitor their activities while connected to the network. modern network security .
• Multifactor authentication, also known as MFA.MFA, an increasingly favored network security option, is a user-friendly solution that utilizes two or more factors to authenticate a user’s identity. Google Authenticator serves as an example, as it generates distinct security codes that users input along with their password to validate their identity.
• Network segmentation. Organizations that have extensive networks and a high volume of network traffic frequently utilize network segmentation ICS) traffic and allowing for better protection against cyber threats. By implementing network segmentation, organizations can better identify and monitor traffic within their ICS, enhancing security measures and reducing the potential impact of cyber attacks. ICSes Internet-connected systems (ICSes) face a higher vulnerability to cyber threats due to their growing integration with cloud computing.
• Sandboxing. protected environment, organizations can safely inspect the file for malware before allowing it to connect to the network. sandbox An organization has the ability to monitor if the file behaves maliciously or exhibits any signs of malware.
• The field of security information and event management, also known as SIEM, involves the management and analysis of security-related data and events.This method of security management records information from both applications and network hardware and observes for any questionable actions. If an abnormality is identified, the system will take action. SIEM The organization receives notifications from the system and responds accordingly.
• Software-defined perimeter (SDP) is a term used to describe a security framework that allows organizations to dynamically create and secure isolated networks for users and devices accessing applications and data. An SDP The aforementioned paragraph can be paraphrased as follows: “A security technique is employed to safeguard a network by hiding it from potential attackers and unauthorized users. This method employs specific criteria to control access to resources and creates a virtual barrier around interconnected resources.”
• A virtual private network, also known as VPN, is a network that allows users to connect securely over a public network, such as the internet. A VPN A virtual private network (VPN) ensures a secure connection between a device and a company’s network. It employs tunneling protocols to encrypt data transmitted over an insecure network. Remote access VPNs allow employees to access their organization’s network remotely.
• Web security. This procedure manages and monitors the internet activity of employees on the network and devices of a company. It involves restricting access to specific threats and websites, as well as safeguarding the security and reliability of the company’s own websites.
• Wireless security. strict security measures and closely monitor wireless networks due to the high level of vulnerability they possess. Adhering to these measures is crucial.Best practices for ensuring wireless security, such as dividing Wi-Fi users based on their service set identifiers, also known as SSIDs, and utilizing the 802.1X protocol. authentication It is important to have effective monitoring and auditing tools in place to guarantee the security of wireless networks.
• Workload security. workload management in cloud and hybrid environments can result in an expansion of vulnerable areas for potential attacks. Implementing security measures for workloads and ensuring their protection becomes crucial. load balancers Ensuring the security of the information held within these tasks is extremely important.
• Zero-trust network access. Similar to network access control, zero-trust In the English language, the provided paragraph can be paraphrased as follows: Only necessary access to perform job responsibilities is given to users through network access, while all other permissions are restricted.
Best Practices for Network Security
- Regular Software Updates: Strengthening the walls and improving the sentries.
- Strong Passwords: Complex, unbreakable seals on the kingdom’s doors.
- Wi-Fi Safety: Using secure channels for communication, avoiding public and vulnerable networks.
- Regular Backups: Having a contingency plan, akin to a secondary stronghold.
- Awareness Training: Educating the kingdom’s inhabitants about potential threats and how to identify them.
The Evolving Landscape of Network Security
In today’s interconnected world, our digital domains have become more complex and intertwined than ever. With every device connected to the network acting as a potential entry point, the need for robust security measures has never been more pressing. From smartphones to servers, each connection is a potential vulnerability, a gate that might be breached by a savvy foe.
Navigating the Challenges of Digital Defense
- Adapting to Evolving Threats: Enemies constantly evolve, requiring vigilance and adaptability.
- Ensuring Regulatory Compliance: Upholding the laws of the land, ensuring the kingdom follows rules and regulations.
- Securing Remote Access: Protecting those who access the kingdom from afar, ensuring no vulnerabilities are introduced.
- Managing Third-party Partnerships: Allies are crucial, but they can also inadvertently introduce weaknesses.
Understanding Network Layers and Their Security
Envision the network as a multi-leveled tower, similar to the OSI model, where each level has distinct functions and vulnerabilities. Effective security demands protection at every level, not just the top or bottom. It’s a comprehensive approach, safeguarding every stratum of the digital infrastructure.
The Complexity of Network Security
Managing network security is akin to ruling a vast, dynamic realm. It involves safeguarding against a myriad of threats – from covert spies (malware) to direct sieges (DDoS attacks). The landscape of network security is perpetually shifting, with new challenges and threats emerging constantly. Yet, with the right combination of tools, strategic thinking, and continual vigilance, this digital kingdom can not only withstand these threats but thrive amidst them.
The Role of Network Security in the Modern World
In our digitally-driven age, the role of network security has expanded far beyond its initial scope. It’s no longer just about safeguarding data; it’s about ensuring the continuity of operations, maintaining customer trust, and upholding a company’s reputation. As technology continues to evolve at a breakneck pace, the strategies and tools of network security must evolve with it.
Balancing Accessibility and Security
One of the critical challenges in network security is striking a balance between accessibility and protection. On the one hand, networks must be accessible enough to allow smooth operation and user convenience. On the other, they must be secure enough to ward off any potential threats. This balancing act is akin to keeping the kingdom’s gates fortified yet functional.
The Future of Network Security
As we look to the future, the importance of network security is only set to increase. With the advent of technologies like the Internet of Things (IoT), artificial intelligence (AI), and machine learning, the digital landscape is becoming ever more complex and interconnected. These advancements, while beneficial, also bring new security challenges and vulnerabilities.
Emerging Trends in Network Security
Emerging trends in network security include the increased use of AI and machine learning for threat detection, the growing importance of securing IoT devices, and the shift towards cloud-based security solutions. Additionally, the concept of zero-trust security models is gaining traction, emphasizing the need to not automatically trust anything inside or outside the network perimeter.
Network Security: A Continuous Journey
In conclusion, network security is not a destination but a continuous journey. It requires ongoing vigilance, adaptation, and education. As the guardians of the digital realm, it’s our responsibility to stay informed, prepared, and proactive in our defenses. By doing so, we ensure that our digital kingdoms remain safe, secure, and prosperous.
Final Thoughts
The realm of network security is vast and complex, but it’s also fascinating and critical. It’s a field that constantly challenges and evolves, requiring a mix of technical expertise, strategic foresight, and a deep understanding of the digital landscape. As we continue to advance into the digital age, the role of network security becomes ever more integral to our lives, businesses, and societies. In safeguarding our digital domains, we protect not just data, but our way of life.
