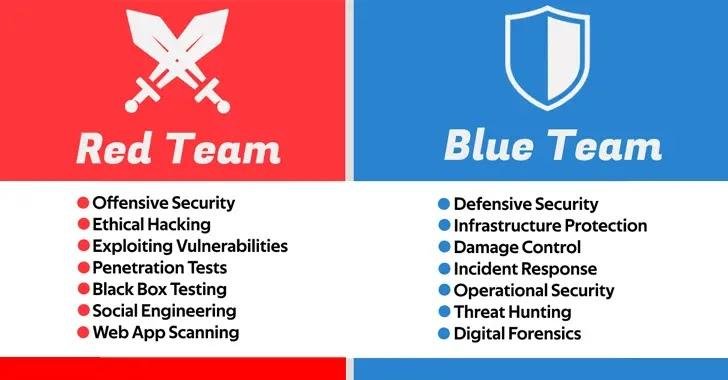
Security is a complex area with various responsibilities and tasks. This article aims to explain and clarify the roles of the red and blue teams in the field of security.
Firstly, what is the reason behind the necessity to divide security responsibilities for two teams on Penetration Testing ?
technology and specialized knowledge. With this approach, these organizations can ensure that all aspects of their security, such as physical security, cybersecurity, and risk management, are adequately addressed by professionals who are knowledgeable and experienced in those specific areas. Therefore, by delegating specific security responsibilities to different units, organizations can establish a comprehensive and robust security framework red team tools .
These are usually called the Red team vs Blue team We will extensively explore and comprehend the definitions of both concepts, the specific responsibilities they undertake, and the level of significance they hold.
The Blue Team: Defenders
- SOC Analyst
- Incident Responder
- Analysts specializing in digital forensics and incident response.
- Threat Intelligence Analyst
- A person who specializes in analyzing and reverse engineering malware.
The security department’s blue team members are experts in safeguarding the organization’s valuable resources.Their responsibility is to guarantee the security and update of systems for every company., overseeing the actions of hackers in order to identify harmful indicators, as well as carrying out numerous intricate procedures.
Blue teaming requires the assurance and upkeep of robust product security, necessitating the establishment of various roles.
Blue Team Tasks

Now, we will examine some of them below.
SOC Analyst
SOC stands for “ Security Operations Center ” A specialized team within an organization, the sub-department consistently watches out for any abnormal activities. The responsibility of these SOC analysts is to act as the initial defense, vigilantly monitoring various resources to identify any potentially harmful incidents.

SOC Analyst
Incident Responder
SOC analysts to investigate and mitigate the risks. incident responders to take it forward with the help of incident response tools .
There are specific guidelines and strict protocols that need to be adhered to for effective containment and escalation procedures following an incident. These steps are typically a part of a CSIRT framework.
Incident Responder
Paraphrased: Analysts specialized in digital forensic and incident response.
system analysis, and malware analysis. These professionals examine objects and data that may be related to the incident, in order to understand what happened and determine the extent of the damage. They also investigate the methods used by attackers and work towards preventing future incidents by improving security measures. event logs analysis In English, the paragraph could be paraphrased as follows: The investigation involves various techniques such as examining the file system and analyzing any evidence left behind to understand the methods used in the attack and conduct a comprehensive investigation.
Threat Intelligence Analyst
Once the data regarding cybersecurity has been gathered and examined to comprehend the motives and techniques of cyber criminals, the resultant information is referred to as threat intelligence.
IOCs), which are pieces of evidence that an attack has occurred or may occur. These analysts collect and analyze data from a variety of sources, such as logs, network traffic, and cyber threat intelligence feeds. By doing so, they can identify patterns and trends that could indicate a potential threat. This information is crucial for organizations to proactively defend against attacks and anticipate future threats. IOCs The aim is to group and classify these IOCs based on different identified threat actors, enabling their use in detecting hackers when encountered again in the future.
The creation of rules and signatures by IT analysts is done to identify specific patterns through the examination of current threat intelligence.
Threat Intelligence
A professional who specializes in examining and deciphering malicious software.
Typically, when cybercrimes occur, they are carried out by sending a type of malicious software that infiltrates the system of the target.
enables us to analyze and understand the inner workings of malware, improve our defenses against it, and raise awareness about its existence. By deconstructing and studying malicious software, we gain insight into its functioning, allowing us to develop better protective measures. most malware analysts do.
Blue teams have a wide range of commonly recognized roles, although the list is not limited to these. Countless other activities, both technical and non-technical, also play a role and are connected to blue team operations. Administration, hazard, and conformity to keep an organization safe.
Numerous responsibilities often intertwine in this field: an individual specializing in malware analysis may also engage in threat hunting, intelligence gathering, or incident response tasks involving detection and mitigation of attacks.
group. When you are part of a group, you are always doing multiple things. blue team This results in increased knowledge and personal development as an individual.
While the blue teamers prioritize system security, they do not rely on waiting for a hacker attack to identify system vulnerabilities. Experienced blue teamers understand that attacks and breaches are bound to occur.
In order to outsmart online criminals, there is an additional security team at work – the Red team. Let’s now delve into what this team is all about.
The members of the Red Team serve as ethical advisors.
Red teamers They have the responsibility to carry out security actions as if they were an attacker, essentially simulating an adversary.
The work they do varies from conducting small security tests on specific applications to carrying out extensive tests on a larger scale or engaging in comprehensive red team exercises.The dissimilarity that exists between penetration testing and red teaming can be explained as follows in the English language. .
said that pentests are the act of conducting individual tests on products in order to identify any weaknesses or vulnerabilities they may have. These tests aim to uncover any potential security flaws present in the products being tested. mobile app pentesting , Web application penetration testing refers to the examination and evaluation of a web application’s vulnerabilities and security measures. or thick client pentesting .
The traditional method for testing applications is being replaced by red teaming, which better meets current needs because it considers all possibilities.
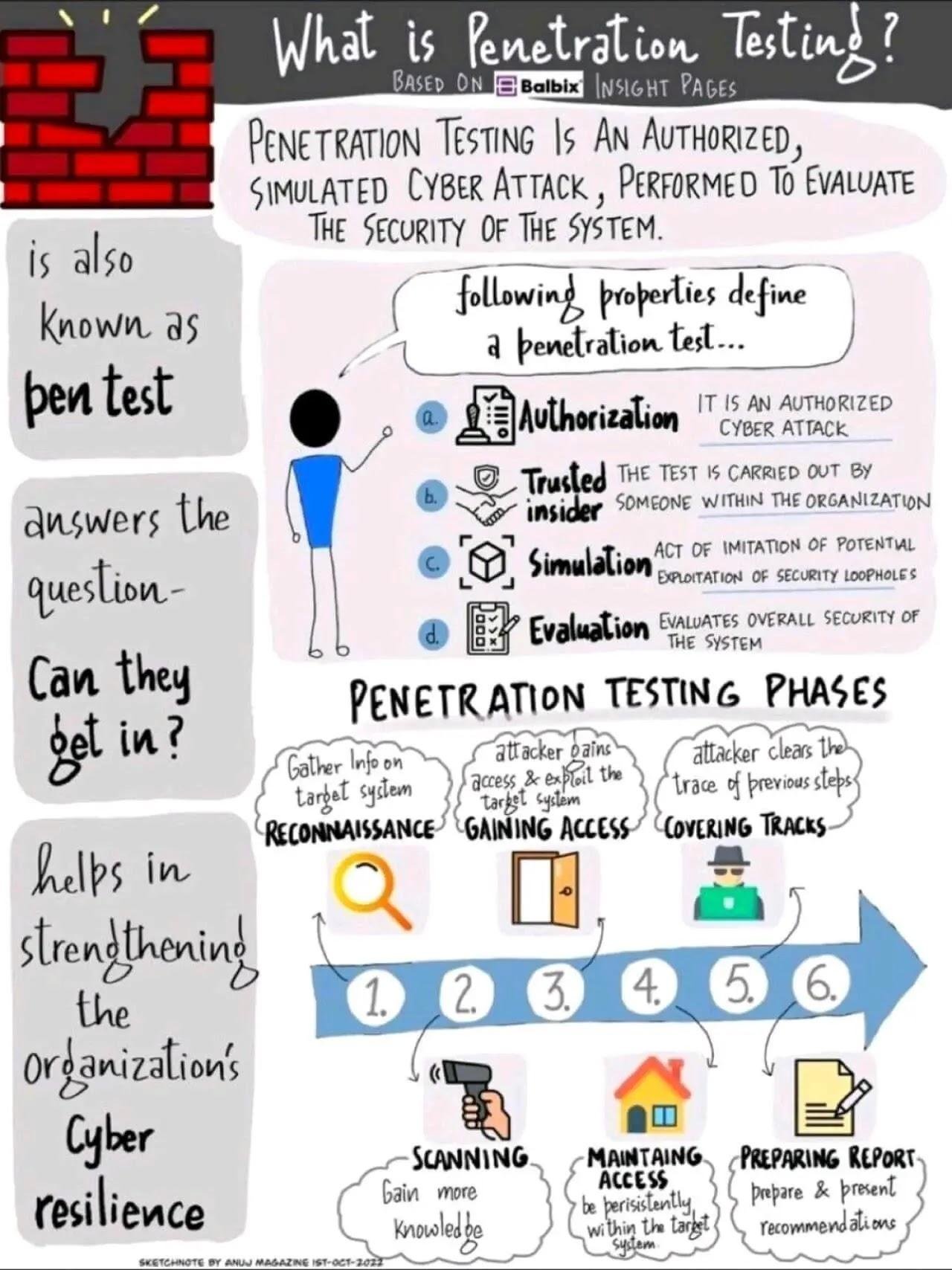
Pentesting
and other deceptive tactics to manipulate individuals into revealing sensitive information or carrying out actions that benefit the operatives. These individuals are often targeted because they may have access to valuable data or resources. OSINT , and they can also attempt to breach physical barriers in order to gain access. Their primary objective is to carry out extensive offensive operations.
In essence, red team operatives and pentesters both play a role in offensive security. Red team operatives have a broader scope, covering a wide range of attack surface, techniques, and tactics. On the other hand, pentesters are more concentrated on a specific scope and delve deeper into the details.
Although blue teams have specific roles assigned to them, red teams do not have such distinct divisions. One possible reason for this is that the red team functions as a cohesive unit with a singular objective, which is to undermine the product.
For example, The red team only needs to find one unlocked lock, while the blue team must make sure that all the locks are locked and secure.Introducing various roles within the red team can pose challenges in terms of management and potentially reduce the operation’s effectiveness.
Nevertheless, skillsets can vary among individual workers.
For example, o One member of the red team could possess exceptional expertise in examining source code and conducting white box testing., there are some individuals who may specialize in hacking into a web application.
A group of diverse individuals with various abilities join forces to create a strong red team, aiming to challenge and carry out attacks against the blue team.
Red Team

During the execution of red team operations, the blue team consistently monitors the ongoing progress to determine if they can prevent any potential threats. If unable to do so, they collaborate with the red team to identify the vulnerabilities in the security system and jointly implement solutions.
The process goes on when a company introduces new products, tools, and workflows into its system. It is advisable to allow your own team to simulate a hack, uncover vulnerabilities, and fix them rather than being exploited by external attackers and dealing with severe repercussions.
We extensively explored the notions of red and blue teams in the field of security, examining their roles, motivations, and significance for any given organization.
However, there is one element that is extremely important for the functioning of both teams: communication. When there is no effective communication between the red and blue teams, the entire operation collapses.
Although there are different communication and data gathering tools, the conventional ones do not have the required capabilities to match the rapid advancements in the security industry.
Hexway provides a comprehensive solution designed for both red teams and their clients. Their red team tool enables the gathering of data into a single location, facilitating seamless collaboration among team members.
The ability to import from various tools and formats enhances data aggregation. Moreover, these tools offer features like tool integrations that enrich the work process.checklists , reporting tools, creating issues and merging them , and many other things.
Ensure that clients receive complete information regarding discovered vulnerabilities through the use of Red team tools, enabling them to promptly initiate the necessary steps for resolving the identified issues.
Conclusion
Security is a significantly extensive realm wherein the adversaries and defenders always operate on different levels due to the constant unveiling of new exploits, attacks, and vulnerabilities.
To effectively protect organizations, their security teams must remain vigilant and ready to handle any potential intrusion. This is why both red and blue teams are essential, as they possess different sets of roles and responsibilities.
We thoroughly studied the basic principles of both teams and recognized their great significance in safeguarding against cyber criminals. We also learned about the valuable role played by pentesting tools in enhancing the security operation process. These efficient tools can be a game changer for pentesters, seamlessly integrating into your PTaaS workflow and empowering your teams to outwit malicious actors.