Accenture has adopted an industrialized approach to enhance its cloud controls

Transforming its initial security challenges into a streamlined compliance process. The company’s cloud journey, starting in 2015, led to a significant expansion of its cloud footprint from 9% to 90% for all business applications within the first year. However, as ...
Read more
Exploring the World of RFID Hacks: The Flipper Zero Phenomenon

In the ever-evolving landscape of cybersecurity, the prevalence of RFID-controlled locks in various establishments across the US has brought to light a curious device – the Flipper Zero. This gadget, seemingly unassuming, has sparked significant attention for its ability to ...
Read more
Cybersecurity Experts: What You Need to Know About EV Charger Hacking and How to Protect Your Vehicle

This story was co-published with Grist. In the evolving world of electric vehicles (EVs) and their infrastructure, cybersecurity has become a critical concern. This comprehensive look dives into the vulnerabilities and efforts to fortify EV charging stations against potential cyber ...
Read more
Privacy Breach: Millions of India’s Vaccine Database Vulnerabilities Exposed.
Personal information, including ID documents Aadhar card number details and phone numbers, have been released on Telegram. In today’s digital age, the security of personal data is a growing concern, and a recent incident in India has brought this issue ...
Read more
Navigating the Startup Journey: Insights and Strategies for Success

The journey into the world of startups is a thrilling and multifaceted adventure. It’s a period where you, as an entrepreneur, dive into new environments, tackle challenges head-on, and innovate ways to grow your business. The essence of startup life ...
Read more
Understanding TAC Control Policy for 5G Private Network Area Restrictions
5G Technology Significance: The advent of 5G technology marks a significant leap in the world of telecommunications. Unlike its predecessors, 5G offers unparalleled speed, reduced latency, and the ability to connect a vast number of devices simultaneously. This technology is ...
Read more
The Limitations of Traditional Cybersecurity Approaches to Generative AI

Critical Flaws Exposed in OpenAI’s ChatGPT and Google’s Bard In the fast-paced and ever-evolving cybersecurity landscape, a new challenge is rapidly gaining prominence: the vulnerability of large language models (LLMs) like OpenAI’s ChatGPT and Google’s Bard to “indirect prompt injection” ...
Read more
Hackers Exploit New Security Flaws in pfSense Firewall Software – Update Immediately

Understanding the Latest Security Vulnerabilities in pfSense The open-source Netgate pfSense firewall solution, a popular tool for network security, has been found to contain multiple security vulnerabilities. These flaws, if exploited, could allow attackers to execute arbitrary commands on vulnerable ...
Read more
RED TEAM and BLUE TEAM Cybersecurity Testing
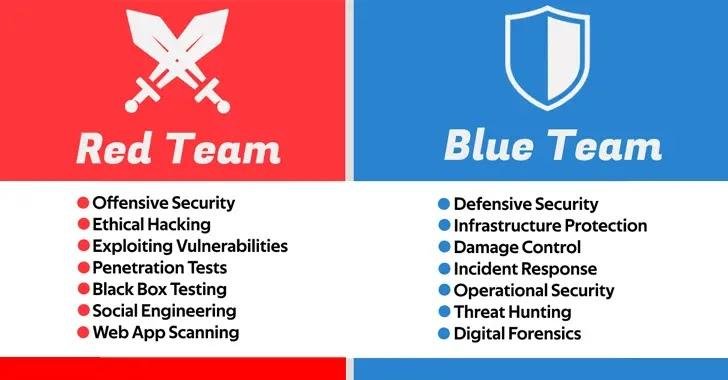
Security is a complex area with various responsibilities and tasks. This article aims to explain and clarify the roles of the red and blue teams in the field of security. Firstly, what is the reason behind the necessity to divide ...
Read more
Google is facing scrutiny over its demonstration video for its newly launched artificial intelligence model, Gemini.

Google’s latest AI model, Gemini, is causing controversy for the company. The AI model, which was launched recently, has been criticized for an edited demonstration video that appears to show it recognizing visual and verbal cues from a person in ...
Read more
